



Key Features & Technologies:
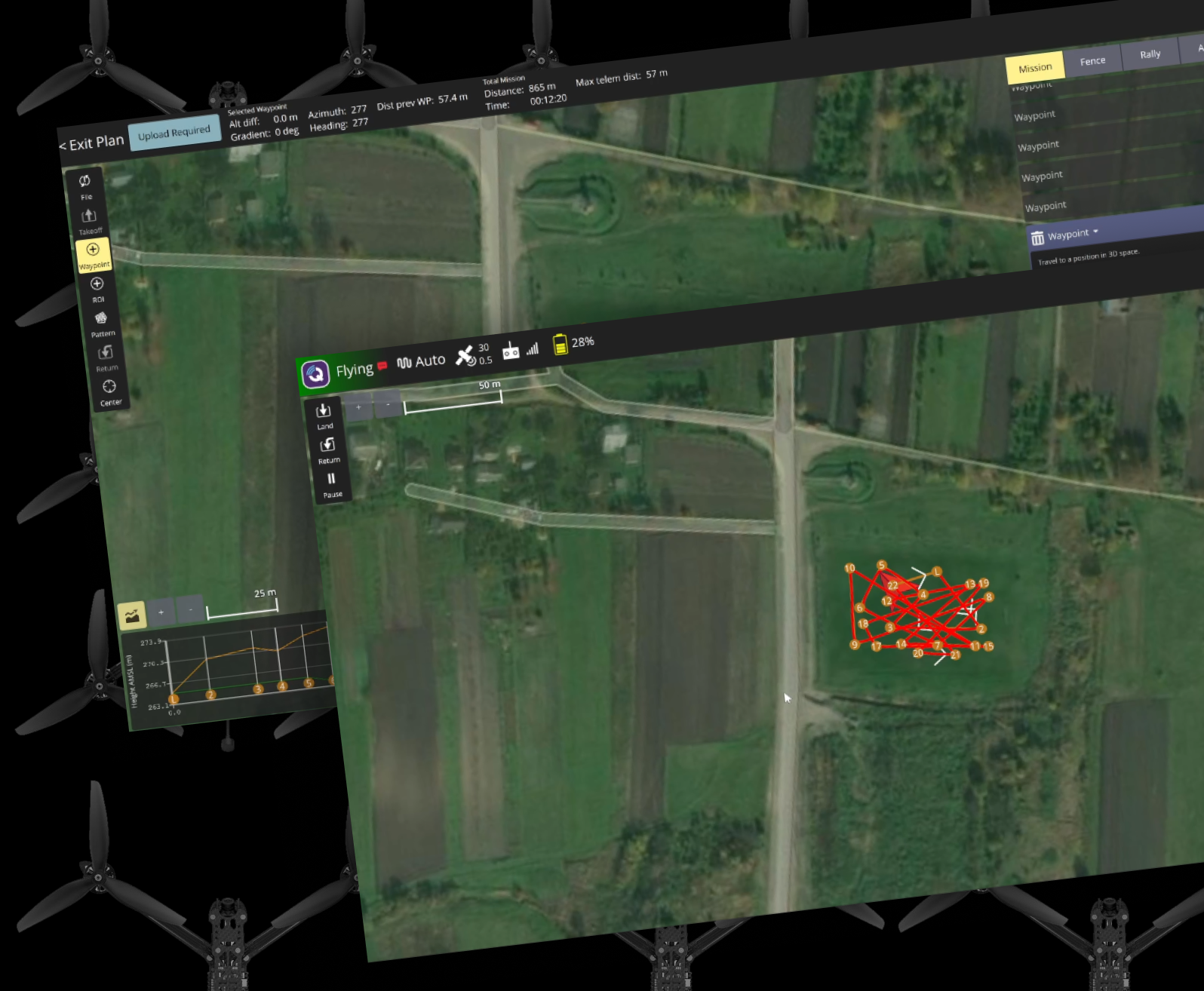
The AI-driven platform analyzes data collected by drones to detect explosive devices and automatically mark cleared zones on operational maps.
Using NVIDIA GPUs and computer vision models (object detection, segmentation, change detection), it processes images and video in real time, generating precise annotations.
The system is designed for seamless continuous integration with existing operational command systems, allowing military units to coordinate responses and track cleared areas efficiently.
Key Features & Technologies:
Because defense software development solutions handle sensitive and classified data, they must comply with strict international and national standards. These typically include frameworks such as NIST, ISO/IEC 27001, and the US Department of Defense’s Cybersecurity Maturity Model Certification.
Adherence to these regulations ensures not only the security of information but also global interoperability of the developed systems.