10 AWS Security Best Practices
#1 Learn How to Use the AWS Well-Architected Framework.
Half the work is done if you have a clear grasp of your security job and duties in the shared responsibility model. Then among the first topics, you need to learn if you’re just getting started with AWS would be Well-Architected Framework. This will assist you in gaining a better capability to make the most of cloud service and discover AWS security best practices and recommended principles to defend yourself against cloud security dangers in the security area. Domain-specific lenses, hands-on labs, and the AWS Well-Architected Tool are all part of the AWS Well-Architected Framework. The AWS Well-Architected Tool, which is accessible for free in the AWS Management Console, allows to evaluate workflows on a routine basis, anticipate potential concerns, and track progress. AWS Well-Architected can help to find out if your architecture is compliant with cloud best practices and get recommendations on how to improve it.
#2 Build a Cybersecurity Strategy
Prior to installing tools and controls, it is necessary to develop a well-thought-out security strategy. It’s critical to have an AWS cloud security plan. If you stick to this sequence, you will be able to assess in practice, when you refer to an instrument or control, whether it supports your strategy. It also enables integration security through all corporate operations, including those that use AWS. Design and implementation a security plan early might also help with continuous deployment. One thing to keep in mind when first moving to the cloud is that traditional security solutions will not be able to provide you with the right cloud security. In such a situation, it is a state-of-the-art strategy that will be able to provide ongoing protection. In case you’re already using AWS for development, setting a clear cloud security plan can help keep your company safe in the booming environment of Continuous Integration/Continuous Delivery. It is of the utmost importance to make sure that everyone in your company is aware of your AWS cloud security policy and is properly educated. One thing to keep in mind when first moving to the cloud is that traditional security solutions will not be able to provide you with the right cloud security. In such a situation, it is a state-of-the-art strategy that will be able to provide ongoing protection. You need to make sure that everyone in your organization is informed about the AWS cloud security strategy and trained accordingly. With this attitude, you can embed cloud security into all phases of the development process. By doing so, you can maintain compliance and be more proactive in preventing attacks. Putting cybersecurity strategy first, every action you take will drive your security positioning.
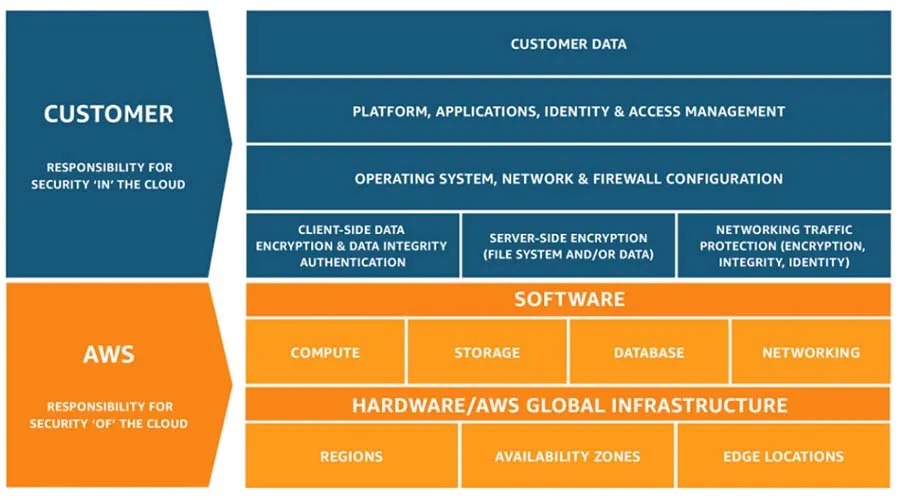
#3 Enforce and Implement Security Controls in the Cloud
It is your responsibility to secure your workloads, so it is up to you to take steps to protect customer and company data from malicious attempts. In order to minimize the risk of data leakage you should:
- Define user roles clearly. Do not give people more access than they need simply give them enough they need to do their duties.
- Conduct audits of privileges. Once users no longer require rights, revoke them. This may be carried out by conducting routine privilege audits that match your workers’ privileges to their current responsibilities.
- Create a password policy that is both strong and easy to remember. The password policy not only should enforce the use of strong passwords, but also the expiry of such passwords. Customers would have to reset their passwords every few weeks or months in this manner.
- Utilize multi-factor authentication (MFA) and authorization time-outs. MFA and connection time-outs give an additional degree of protection to your AWS environment by making it more difficult for hostile actors to access accounts.
These AWS security best practices will assist to mitigate some of the risks associated with poor security hygiene, making it more difficult for unauthorized users to access your files. However, these measures will only be effective unless you are consistent in your enforcement and ensure that these controls are implemented across your firm. Moreover, only give root access to users if it’s really necessary. Keep your AWS account’s root user access keys safe. Maintain it in a secure area that only you are aware of.
#4 Make CloudTrail Security Configurations Stricter
CloudTrail is an AWS security service that creates log files for all API calls performed through the AWS administration dashboard, SDKs, and command-line tools. For compliance auditing and post-incident forensic investigations, this functionality allows enterprises to continually monitor activity in AWS. An S3 bucket is used to store the produced log files. One of the first things a malicious attacker will have if they obtain access to an AWS account is to disable CloudTrail and remove the log files. For taking full advantage of CloudTrail, businesses need to:
- To avoid monitoring and management voids, allow CloudTrail across all geographic areas and AWS services.
- Turn on CloudTrail log file validation to guarantee log integrity of information by tracking any changes done to the log file once it has been sent to the S3 bucket.
- To track access requests and identify possibly unwanted or unjustified login attempts, activate entry logging for the CloudTrail S3 bucket.
- To erase CloudTrail S3 buckets and encrypt all CloudTrail log files in flight and at rest, use MFA.
#5 Apply Best Practices for Identity and Access Management
Identity and Access Management is an Amazon feature that allows users to provide users and regulate access to their accounts. IAM allows administrators to create and manage AWS users and groups, as well as apply precise authorization restrictions to individual users and groups of users to restrict access to AWS APIs and resources. Organizations need to make the maximum use of IAM:
- To reduce the chance of an individual user gaining excessive and superfluous access or privileges through mistake, tie IAM rules to groups or roles rather than individual users when designing them.
- Instead of supplying a unique username and password for access, use IAM roles to guarantee that forgotten or hacked credentials do not result in unauthorized access to the resource.
- Ascertain that IAM users have limited access to AWS resources while still being able to perform their job duties.
- Guarantee that all IAM users have multi-factor authentication enabled for their accounts as a final line of protection against a hacked account, and restrict the number of IAM users with administrative access.
- To ensure that data cannot be accessed with a potential lost or stolen key, rotate IAM access keys on a regular basis and standardize on a certain number of days for password expiration.
- Adopt a strong password policy that requires a minimum of 14 characters, one number, one upper case letter, and one symbol. Implement a password reset policy that bans users from reusing a password they’ve already used in the last 24 password resets.
#6 Maintain Security Best Practices with AWS Databases and Storage Services
The spate of AWS data leaks caused by misconfigured S3 Buckets has highlighted the need of ensuring the security of AWS data storage services at all times. Clients can utilize Amazon RDS relational database, Aurora MySQL relational database, DynamoDB NoSQL database, Redshift petabyte-scale data warehouse, and ElastiCache, among other database services in-memory cache. With its Elastic Block Store and S3 services, Amazon also provides data storage. Here are some AWS security best practices around AWS database and data storage security:
- Unless the company requires it, make sure no S3 Buckets are publicly legible.
- To assist auditing and post-incident forensic investigations for a specific database, enable Redshift audit logging.
- As an extra degree of protection, encrypt data stored in EBS.
- As an extra degree of protection, encrypt Amazon RDS.
- To reduce the danger of a man-in-the-middle attack, enable the required SSL option in all Redshift clusters.
- Decrease the risk of harmful actions including brute force assaults, SQL injections, and DoS attacks by restricting access to RDS instances.
#7 Remember to Employ Encryption
The importance of encryption in AWS security cannot be stressed enough, because it serves as another security hurdle that reinforces your security position. Ideally, it is better to encrypt all of your data, not just certain types of sensitive data for regulatory compliance purposes. This entails encrypting data in transit as well as data saved on S3. Within AWS’s cloud infrastructure, encrypting data is simple. To safeguard data stored on S3, just utilize their inherent encryption capability. Client-side encryption is also a smart option for protecting your data before it travels to the cloud. By encrypting both the server and the client, you’ll get an extra layer of security.AWS’ Key Management Service allows you to manage your encrypted files from a single location. It will be considerably easier to manage your keys if you use client-side encryption in conjunction with server-side encryption.
#8 Make Backups of Your Data
Providing regular data backups is one of the important AWS security policies. After all, you can never know if you will need to recover data after a leak. AWS Backup is among Amazon web services that allow for the user to automate backups in an AWS environment, ensuring that you never lose vital data. Each company needs its own backup strategy. AWS Backup provides a variety of backup and restoration options to meet your specific data and regulatory requirements. The type of your data, your present IT architecture, and your industry need all influence your AWS backup plan.
#9 Maintain AWS Systems Updated
Even if your AWS cloud servers aren’t publicly visible, it’s critical that you maintain them patched on all occasions. Dealing with out-of-date cloud infrastructure might expose you to a variety of security risks. And such flaws might result in a cybersecurity breach that damages your company's huge amounts of money. You may patch your AWS servers using a variety of third-party solutions. Alternatively, you may utilize AWS Services Manager Patch Manager, which makes patching your cloud systems simple.
#10 Employ a Cloud-based Security Solution
Typical security solutions are unsuccessful at safeguarding your cloud assets because they were not built to cope with the intricacies of the cloud. So should entrust the security of your AWS cloud to a native cloud solution that:
- Provides a high level of security that allows for continuous delivery.
- Would you be capable of defending your AWS workloads from outside threats?
- Gives you a better picture of your cloud architecture.
Furthermore, a number of excellent native cloud security solutions are developed to assist you in meeting a variety of regulatory standards. This improves your security posture and makes following the AWS recommended practices we’ve discussed in this post easier.
How to Create an Effective AWS Security Policy
In comparison to typical on-premises systems, cloud security necessitates a new set of policies and technologies. To optimize the protection of their AWS installations against cyber threats, organizations must adapt their security approaches to the dynamic and flexible nature of cloud-based deployments and adopt cloud-native security solutions.
Firstly, enhancing your company’s cloud security is to identify any current security holes that might expose it to attack. Such a self-guided assessment generates a prioritized list of actions to take to remediate any identified issues, including a full security report auditing over hundred compliance requirements, checks for security misconfigurations within your AWS deployment, providing a complete inventory of AWS assets, and generating a full security report auditing over hundred compliance requirements.
The next step is to remedy those holes in your organization’s present AWS security posture after detecting possible gaps and concerns. inVerita suggests cloud-native solutions that may assist automate your organization’s cloud security while also delivering complete cloud protection and enhancing the security team’s effect. You may also get in touch with us for more information on how the inVerita team can help protect your AWS setup and to schedule a demo to witness it in action.