More and more companies are making a strategic business move to outsourcing. Not limited by geographical borders, they can hire employees from the best talent pools, improve their operational efficiency, and minimize overheads.
Yet, entrusting critical business processes to external providers also introduces potential security vulnerabilities.
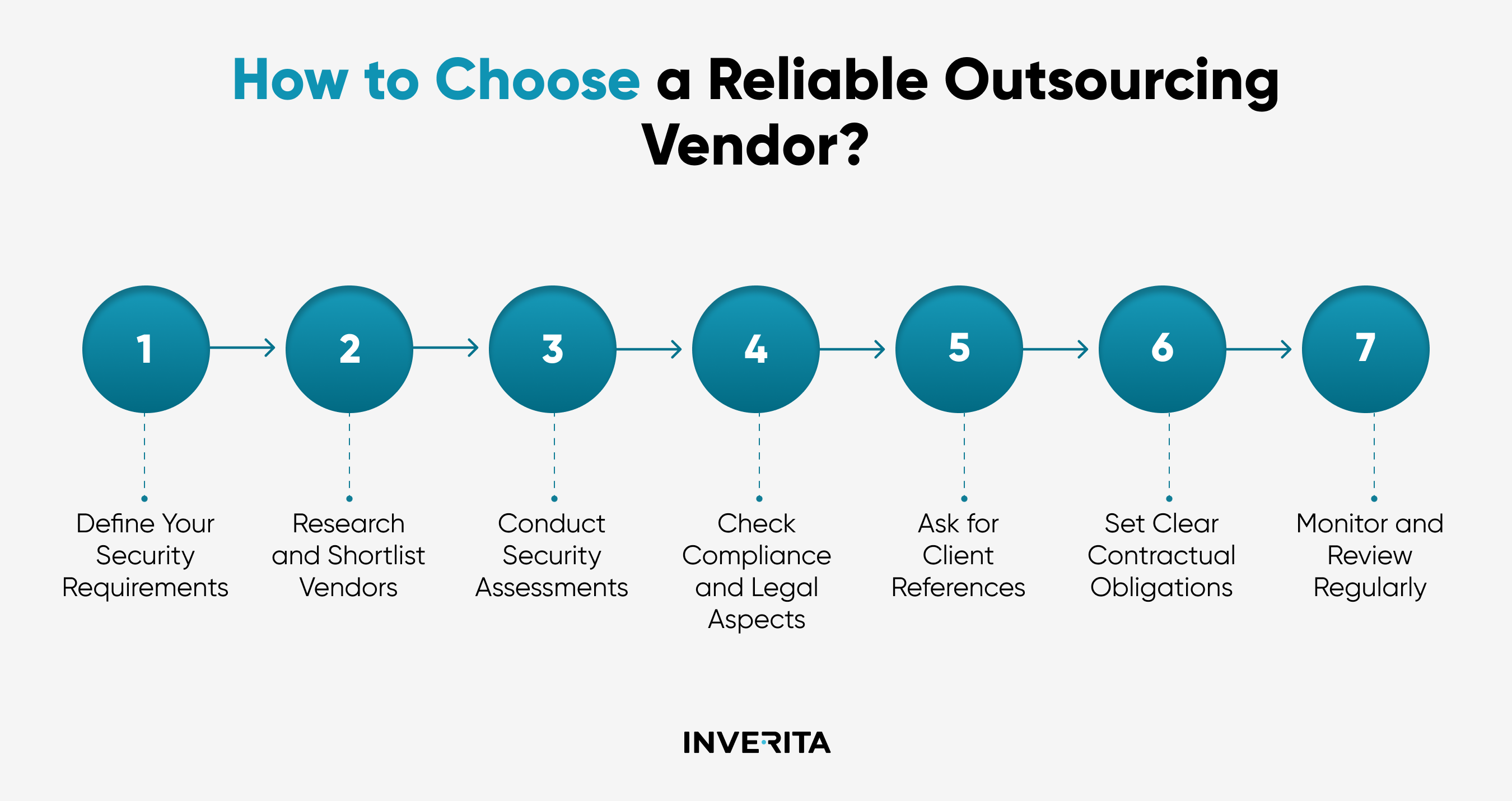
inVerita has been in outsourcing for many years, serving data-sensitive industries like healthcare, finance, and e-commerce. Therefore, in today’s blog, we would like to share our time-tested tips on how to ensure data security in IT outsourcing.
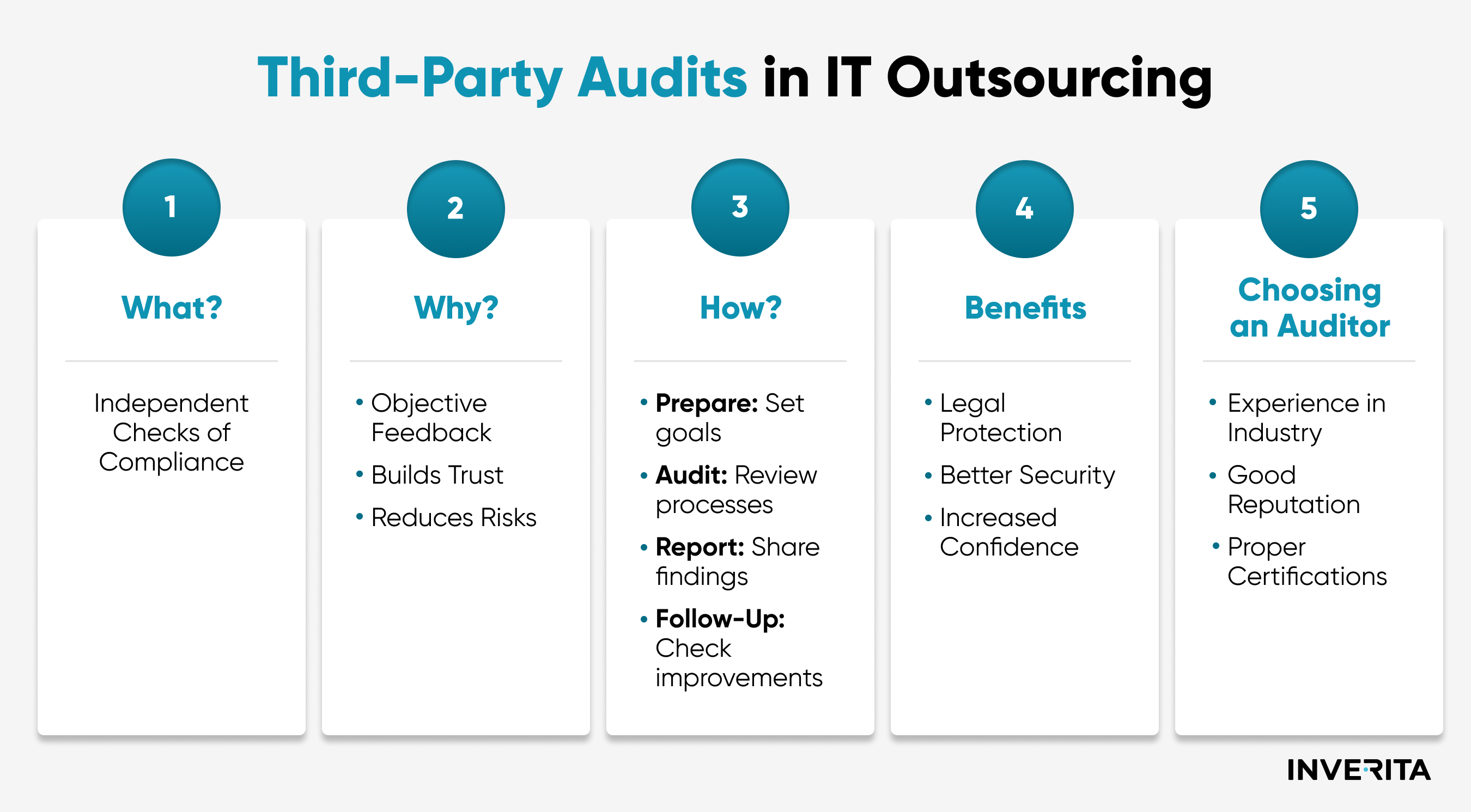
The Importance of Data Security in IT Outsourcing
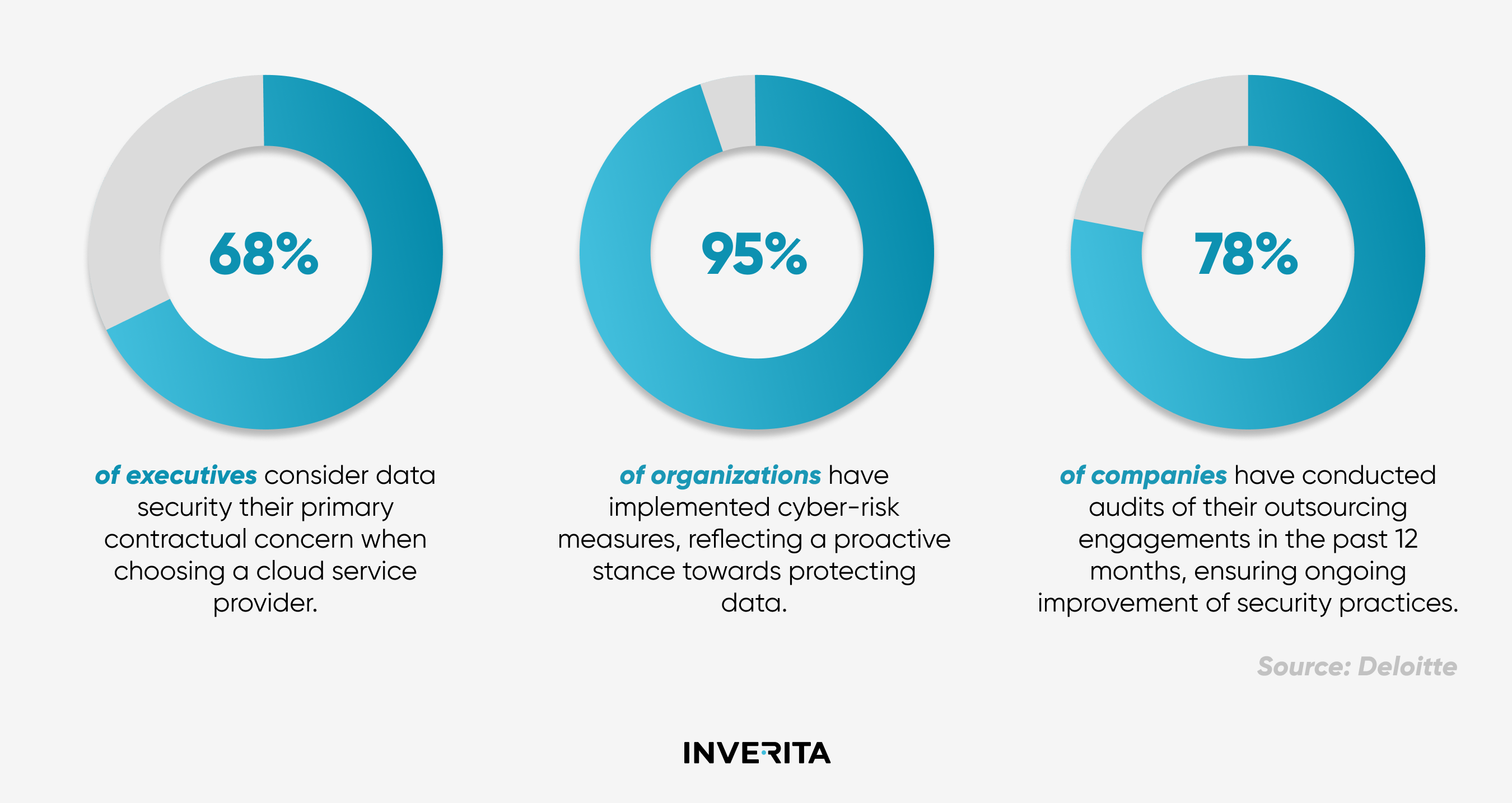
With 71% of businesses globally relying on outsourcing for some of their core business operations, ensuring data security in outsourcing is critical.
According to IBM’s Cost of a Data Breach Report, the average time to detect a data breach is now around 212 days, which gives attackers enough time to exploit vulnerabilities and access valuable information. This delay can lead to not just financial losses but also severe damage to a company’s reputation.
For example, the Target data breach in 2013 is a stark reminder of what can go wrong. The breach exposed the personal and financial information of over 40 million customers, leading to losses of $202 million and a significant dip in consumer trust. The attack originated from an outsourced HVAC vendor, highlighting how security issues with outsourcing can lead to severe consequences.
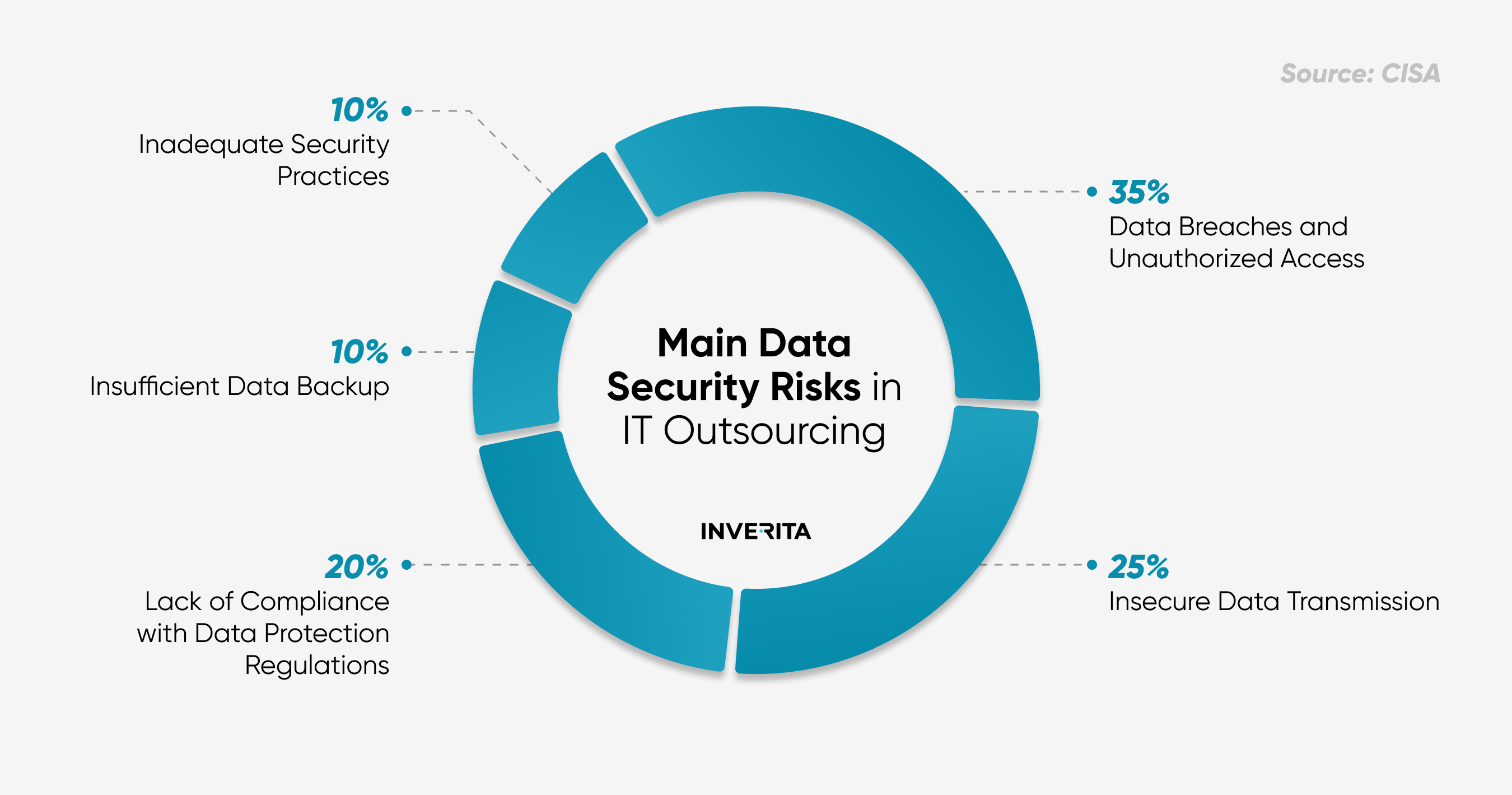
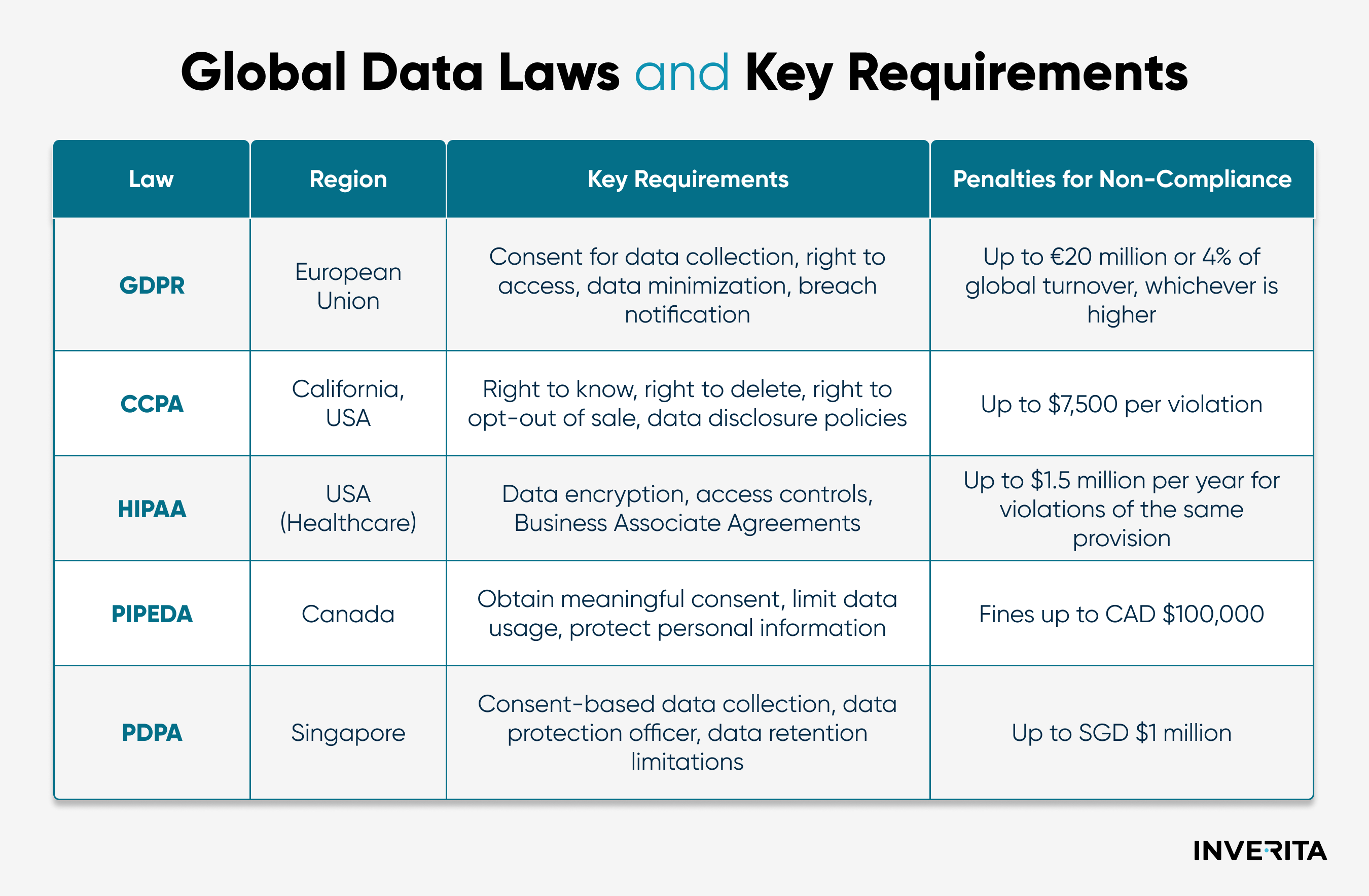
With nearly half of organizations seeing hybrid IT environments as their biggest cybersecurity challenge, companies need to protect data both in-house teams and with outsourced partners. If they don’t ensure data security in IT outsourcing, it can lead to heavy fines, legal issues, and damage to their reputation.